Hey...
psssst! 
Ever wanted to block internet advertising from
within your router?

"Why would I want to do such a thing?", you may ask.
Well, whether you want ad-blocking for your mobile devices while at home (most mobile browsers don't allow plug-ins, including AdBlock), you want to help your WiFi guests escape ads while they're logged in at your place, or you just want a fun evening project hacking around in your router, just follow these steps to ad-blocking bliss...
I got this idea from a few websites and forum posts out there that have elaborate scripts for parsing the above hosts file links, cobbling them into a custom file, and doing it on a regular schedule to keep the hosts file up to date. I wanted to keep it simple, so I just created a hosts file manually and uploaded it to my router, which worked just fine.
First, a few caveats:
1 - It only works on DD-WRT and
it's step-children, and
2 - It's really nothing more than feeding your router an extra 'hosts' file (for more information on that, see
HERE, and
HERE and um...
HERE about that...), so nothing fancy.
3- You have to have "Local DNS" and "DNSMasq" enabled on your router so it can act as a proxy for your network's DNS requests (we'll go over that in this post).
More caveats: I still don't know how to block Youtube ads, and apparently Internet Explorer doesn't really dig URL redirects to empty ether, so some some good folks have come up with something called
Pixelserv that is simply a webserver whose sole purpose in life is to serve back exactly one pixel, so IE doesn't get stuck in a loop actually expecting something back when it calls to the abyss for a non-existent ad URL.
Links to articles describing installing and using Pixelserv and advanced host-file voodoo hijinx at the bottom.
So, let's get started...
First of all, log in to your router and select the "Administration" tab.
(I am using a Buffalo WZR-HP-G300NH with a branded version of DD-WRT. Your interface may differ somewhat.)
It will ask you to log in:
From there, scroll down until you get to the part labeled "JFFS2"
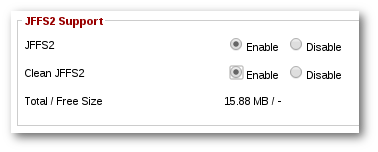
Enable it, and if this is the first time you are doing this, enable "Clean JFFS2" also.
Apply settings:
Don't reboot yet! We will do that later.
Go to the "Services" tab:
and scroll down to "DNSMasq":
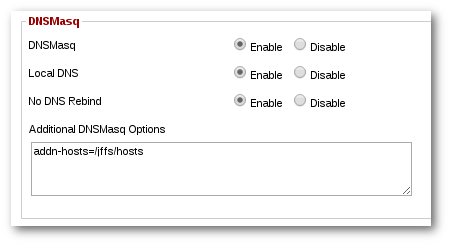
Type in as shown:
addn-hosts=/jffs/hosts
NOW comes the hacker part:
A 'hosts' file is a list of addresses and URLs arranged in a [address] [space]
[URL] format, like so:
127.0.0.1 sleazyadserver.com
127.0.0.1 naughtyadserver.net
127.0.0.1 badguys247.org
So, with your favorite text editor, copy and paste in the host-file entries from the links above, or from the links
HERE, plus any that you would like to include, and edit the redirect address to your liking. Most folks will use 127.0.0.1, some use 0.0.0.0, use whatever tickles your fancy, but remember to save the file with
Unix line endings and plain ol'
ascii text.
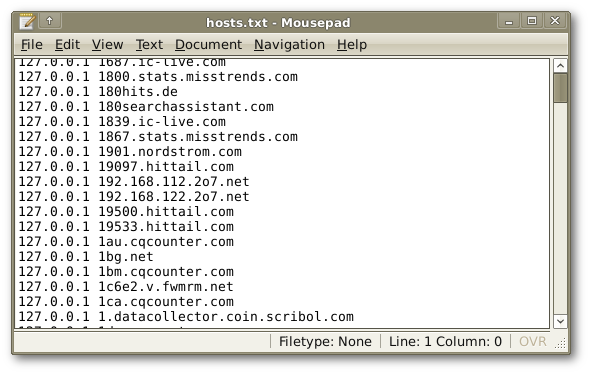
Call it 'hosts.txt' for now.
Now, using 'scp' (if on Linux or BSD) or 'pscp' (PuTTY's implementation of scp on Windows), upload the file to your router.
The syntax for scp is: [scp or path to pscp] [path to the hosts file you created] root@[your router's address]:/path/to/somewhere
From Linux, if I put the hosts file in my home directory, and my router is at 192.168.11.1, it looks like this:
On Windows, if I put the file on my Desktop, it might look like this in a command window (Start Menu -> Run.. -> 'cmd'):
"C:\Program Files\PuTTY\pscp.exe" "C:\users\edvard\Desktop\hosts.txt"
[email protected]:/jffs/hosts
Next, log back into your router via the web interface, click the "Administration" tab, go to the bottom of the page and reboot!
Now, open a command window and try to ping one of the adservers listed in the hosts file:
ping www.clickhouse.com
If you get a response like this:
PING www.clickhouse.com (127.0.0.1) 56(84) bytes of data.
64 bytes from localhost (127.0.0.1): icmp_seq=1 ttl=64 time=0.019 ms
64 bytes from localhost (127.0.0.1): icmp_seq=2 ttl=64 time=0.032 ms
64 bytes from localhost (127.0.0.1): icmp_seq=3 ttl=64 time=0.038 ms
--- www.clickhouse.com ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 1998ms
rtt min/avg/max/mdev = 0.019/0.029/0.038/0.010 ms
... then you're successful. If not, something's not right, and I suggest you go through the steps again, or maybe I got something wrong, and I need your help to de-bug the process. Happy ad-free routering!

References and resources:
Ad blocking from the DD-WRT Wiki, complete with complicated automatic update script and everything:
http://www.dd-wrt.co...ndex.php/Ad_blockingHow-to Geek article on ad-blocking with the Pixelserv:
http://www.howtogeek...pixelserv-on-dd-wrt/Turn your Raspberry Pi into a wireless access point with ad-blocking:
https://learn.adafru...ccess-point/overviewhttps://learn.adafru...ccess-point/overview