This one is fairly serious. It's called "GHOST."
Here's the background info:
GHOST, a critical Linux security hole, is revealed
Summary:This security hole, which impacts many older versions of Linux and some current ones, should be patched as soon as possible.
By Steven J. Vaughan-Nichols for Linux and Open Source | January 27, 2015 -- 19:33 GMT (11:33 PST)
Researchers at cloud security company Qualys have discovered a major security hole, GHOST (CVE-2015-0235), in the Linux GNU C Library (glibc). This vulnerability enables hackers to remotely take control of systems without even knowing any system IDs or passwords.
Qualys alerted the major Linux distributors about the security hole quickly and most have now released patches for it. Josh Bressers, manager of the Red Hat product security team said in an interview that, "Red Hat got word of this about a week ago. Updates to fix GHOST on Red Hat Enterprise Linux (RHEL) 5, 6, and 7 are now available via the Red Hat Network."
This hole exists in any Linux system that was built with glibc-2.2, which was released on November 10, 2000. Qualys found that the bug had actually been patched with a minor bug fix released on May 21, 2013 between the releases of glibc-2.17 and glibc-2.18. <more>
To test to see if you're vulnerable see
this article.
---------------------------------------------------------------------------------------------------------
For those who are new - or new enough to Linux - to not understand the part about compiling, do the following:
1) Copy and past all of the following code into your text editor and save it as
ghosttest.c This is the code
/* ghosttest.c: GHOST vulnerability tester */
/* Credit: http://www.openwall.com/lists/oss-security/2015/01/27/9 */
#include <netdb.h>
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <errno.h>
#define CANARY "in_the_coal_mine"
struct {
char buffer[1024];
char canary[sizeof(CANARY)];
} temp = { "buffer", CANARY };
int main(void) {
struct hostent resbuf;
struct hostent *result;
int herrno;
int retval;
/*** strlen (name) = size_needed - sizeof (*host_addr) - sizeof (*h_addr_ptrs) - 1; ***/
size_t len = sizeof(temp.buffer) - 16*sizeof(unsigned char) - 2*sizeof(char *) - 1;
char name[sizeof(temp.buffer)];
memset(name, '0', len);
name[len] = '\0';
retval = gethostbyname_r(name, &resbuf, temp.buffer, sizeof(temp.buffer), &result, &herrno);
if (strcmp(temp.canary, CANARY) != 0) {
puts("vulnerable");
exit(EXIT_SUCCESS);
}
if (retval == ERANGE) {
puts("not vulnerable");
exit(EXIT_SUCCESS);
}
puts("should not happen");
exit(EXIT_FAILURE);
}
2) Open a terminal session (press: CTRL-ALT-T) and change to the directory where you saved ghosttest.c
3) Compile the file you just saved by entering the following command at the prompt:
gcc ghosttest.c -o ghosttest4) When completed (takes about 1 second) run it with the following command:
./ghosttestHopefully, you'll see output similar to the following:
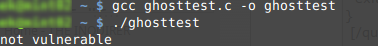
What you're looking for is that "
not vulnerable" at the bottom. If that's the case,
no problem. If you see "vulnerable" check with your distro's website to see the status of where they are with getting out a security patch to correct it. In most cases the patch will be delivered through your distro's update manager when it's available. Which should be very shortly if it isn't available already.
Luck!


(Note: Mint 17.1 should
not be vulnerable. But check your installation anyway just to be sure.)
