3301
General Software Discussion / Re: Cloud-storage - safe & secure? Consider Wuala (it's encrypted as well).
« Last post by IainB on January 03, 2014, 06:53 PM »@ericalynne and @tomos + 2 others, would you like to join in a trial/experiment?
Just to help things along, I have today set up (for FREE) a new ID and Wuala Business account 30-day trial for experimentation and to see how it all works in practice.
If we experiment with this, then we might be able to discover/understand a solution to Erica's problems with Wuala (rather than experimenting on her existing Business account).
The Business account looks like it should be relatively straightforward, but, as they say, "The proof of the pudding is in the eating"!
The company name I have set up for this trial purpose is NJ.Dawood Enterprises. (It is not a real company name/person. Once set, this name cannot be changed.)
The group name I have set up for this is NJ.Dawood Enterprises-DCF Trial. (Once set, this name cannot be changed.)
Now, I would like to get some members on board. I am allowed a max. of 5 members per group, for the trial.
Members can access the group in two ways:
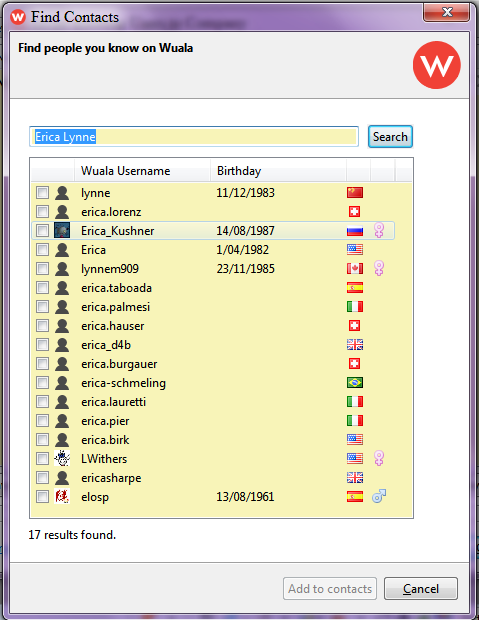
I scanned for existing Wuala member's name "Erica Lynne", and got this result, so am unsure which is the "right" Erica:
I could invite someone specific (e.g., @tomos) to become a new member of Wuala (assuming he isn't one already) and join the group.
Or, I could invite anyone to become a new member of Wuala and join the group via a referral link.
Each time a new Wuala member joins this from an invite of mine, I gather that it will add 1Gb of storage to the account (there is a max limit to accumulate to the account of up to 10Gb this way, I gather).
To incentivise referrals, it will also give the new user 6Gb free to start with, rather than the usual 5Gb for new users.
I'm not sure, but I think for us to experiment with Wuala it is probably only of use for the purposes of examining @ericalynne's situation if we have new/existing Wuala users join the group (max limit = 5 members of a group), as this would reflect Erica's business account "model".
Just to help things along, I have today set up (for FREE) a new ID and Wuala Business account 30-day trial for experimentation and to see how it all works in practice.
If we experiment with this, then we might be able to discover/understand a solution to Erica's problems with Wuala (rather than experimenting on her existing Business account).
The Business account looks like it should be relatively straightforward, but, as they say, "The proof of the pudding is in the eating"!
The company name I have set up for this trial purpose is NJ.Dawood Enterprises. (It is not a real company name/person. Once set, this name cannot be changed.)
The group name I have set up for this is NJ.Dawood Enterprises-DCF Trial. (Once set, this name cannot be changed.)
Now, I would like to get some members on board. I am allowed a max. of 5 members per group, for the trial.
Members can access the group in two ways:
- 1. As existing personal members/users of Wuala. This could be @ericalynne, for example.
- 2. Via a website at a specified URL address and an associated key. (I haven't managed to get this to work fully, yet.)
I scanned for existing Wuala member's name "Erica Lynne", and got this result, so am unsure which is the "right" Erica:
I could invite someone specific (e.g., @tomos) to become a new member of Wuala (assuming he isn't one already) and join the group.
Or, I could invite anyone to become a new member of Wuala and join the group via a referral link.
Each time a new Wuala member joins this from an invite of mine, I gather that it will add 1Gb of storage to the account (there is a max limit to accumulate to the account of up to 10Gb this way, I gather).
To incentivise referrals, it will also give the new user 6Gb free to start with, rather than the usual 5Gb for new users.
I'm not sure, but I think for us to experiment with Wuala it is probably only of use for the purposes of examining @ericalynne's situation if we have new/existing Wuala users join the group (max limit = 5 members of a group), as this would reflect Erica's business account "model".

 Recent Posts
Recent Posts




