You give me some hope if the syslog can be output to the client Windows Event Log though! That could be ideal, if feasible.-IainB
After suggesting that, I've starting playing around with AutoIt3 to see if it can receive the events, (I can already write to the Application EventLog), atm it can see the kernel log restarts from my router. So if it works out, it'll just be a small program that sits around monitoring a port.
... do you have incoming ICMP messages blocked in the router ...
-4wd
I don't know, I never kept a record, and I wouldn't know the difference anyway. As far as I recall, they all look similar in format to the ones in the image.
By default incoming connections should be blocked, (if the router firewall is enabled), so for ICMP messages, (pings), to be getting through there's usually a couple of places to check:
Check Incoming IP Filtering and ensure there isn't an Allow rule for ICMP protocol:
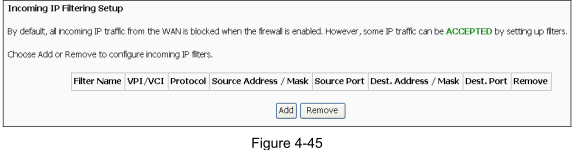
If it's only happening to one particular IP on your network, then you may also have an Allow rule set to Any, (depends on your router whether Any is a valid selection), to that IP.
And there is usually an option somewhere, (in Advanced or Administration), that says something like:
Respond to ICMP requests: Never, LAN, WAN, Both
This is purely to do with what the router does when a ping is directed towards its LAN or WAN IP. Normally you'd set it to Never or LAN unless you have a specific need to ping your router from the internet.
A quick search through the manual for your router for ping or ICMP didn't seem to find anything but that doesn't mean it can't be controlled by logging in via telnet and issuing a command.
I am wondering why your software firewall is seeing a lot of inbound blocking activity if the routers firewall is turned on though, (it does support a
SPIw firewall which should make it reasonably intelligent).
Referring to the W7FC image, you've cut it off so does it report what protocol is being used?
Don't know if this is feasible or worth bothering with, (SJ, 40, etc would be more informed than me), you have connection attempts being blocked to processes started by svchost.exe - it might pay to try and narrow down what processes in particular. Possibly by using
Process Explorer to get the names and trying to correlate with lookups on the blocked IPs.
Addendum: Here's another SysLog Server that might be a bit simpler,
LogLady - very small (2.30MB) and works quite well with my router sending messages to it. LogLady's default port for your router to send to is 514.
Shareware, but you could use it for a short period to see what's what.
 I want to ping back blocked incoming pings - could I use BlackIce Defender?
I want to ping back blocked incoming pings - could I use BlackIce Defender?