| Originally posted: | 2013-09-26 |
| Last updated | 2017-02-08 |
Basic Info| App Name | Interfaith Explorer |
| Description | Religious text repository and referencing system, available in 20 languages. |
| Thumbs-Up Rating |      |
| App URL | Online version: http://bahairesearch.com
Download the client: Interfaith Explorer |
| App Version Reviewed | Several versions, up to and including v2.4.0 (current since 2013-12-30)
- trialled by me in English and also with the French plugin. There are 20 language plugins in total.
|
| Test System Specs | MS Win7-64 Home Premium |
| Supported OSes | PC Windows (various) andiPhones, iPods & iPads |
| Support Methods | Regular updates and access to feedback to/from the application developers. |
| Upgrade Policy | Automatic updates. |
| Trial Version Available? | Not applicable (This is FREEware.) |
| Pricing Scheme | Not applicable (This is FREEware.) |
Intro and Overview:I maybe should apologise, as this review is probably long overdue. I knew I should do it, but had kept putting it off because it takes
work to do that, and I am essentially lazy. However, because I thought the software was good, I have occasionally posted positive comments about
Interfaith Explorer scattered over a few years' worth of discussions in the DC Forum. (If you do a search, you will find them.)
However, yesterday I made a long post about it in a
Basement discussion thread, and in response,
@Renegade commented:
Holy shit!  That looks awesome! Running out to download and check it out....
That looks awesome! Running out to download and check it out....
That really should be posted in the General Software forum. Looks like a very cool piece of software.
______________________
-Renegade
So I am guiltily rectifying matters now.
Rather than write an introduction out from scratch, here is the post from the Basement thread
God's Server that I had made in response to someone else's earlier comment. This should suffice as an introduction, as long as you appreciate that context:
It is said that God is infinite, omniscient and omnipresent - and for all we know that could be true - so by definition he probably can't be "too busy". That is, there would arguably be no queuing involved.
However, that doesn't mean that you can't use computer network servers to spread the word. Previously largely a purely manual process and the domain of "holy men" (rabbis, vicars, priests, imams or their acolytes) spreading the word involved preaching to assembled congregations and reading out passages of various bibles and sacred texts for students/worshippers to recite and learn by rote.
Recite no more. Automation of the manual process and some subsequent enlightenment can now be easily distributed across the network, relatively painlessly. The best example of this that I have come across is via the Bahai faith's website - http://bahairesearch.com
There they have the online Interfaith Explorer, and you can read and cross reference the main books from the main religions.
You want it offline too? No problem. From this superbly informative website, you can download the local client application (for various languages) Interfaith Explorer
Once you have that you can read and cross reference the main books from the main religions on your laptop/PC.
Prepare to be somewhat amazed. Well worth at least an exploratory read.
I reckon that's as close as you are likely to get to an earthly God's server, until you get to go to that Ultimate Data Centre in The Cloud - so make the most of it.
[ Invalid Attachment ]
____________________________
-IainB
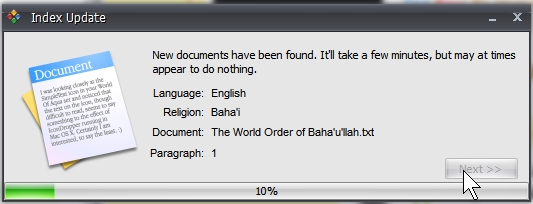
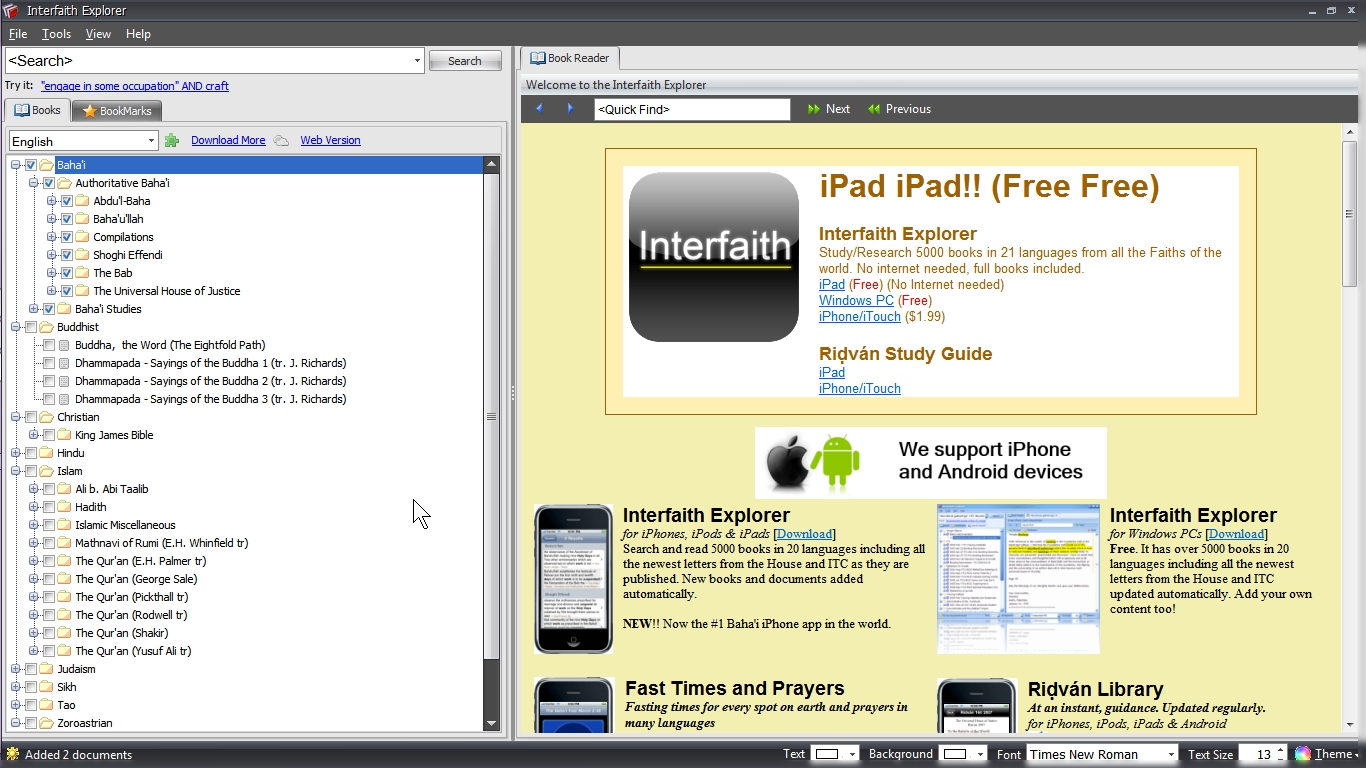
Examples - screenshots/clips:- 1. A typical startup screen
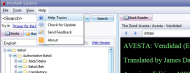
(Enlarged startup update window)
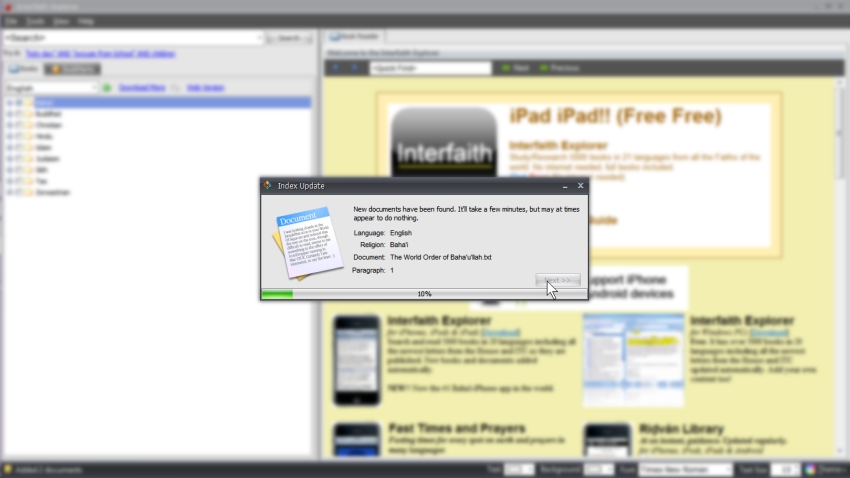
(Main User Interface - English)
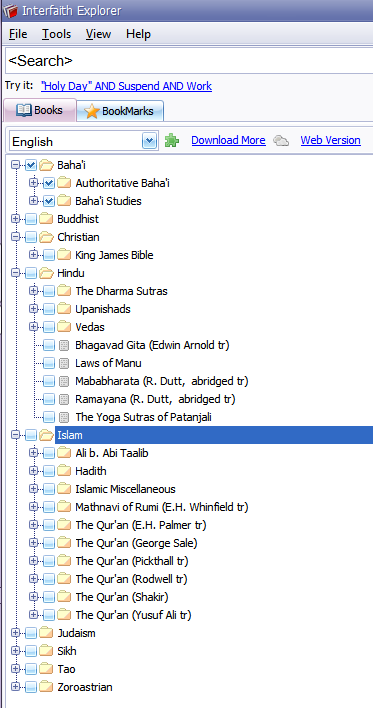
(Left-hand pane showing partly-opened books list)
- 2. Menu examples - French/English - different coloured backgrounds.
________________
________________
________________
Who this software is designed for:Anyone who might be interested in expanding their knowledge of theology, religions, religious books/bibles and comparative theology.
The Good:Incredibly useful and excellent collection and indexed search capability of the important religious texts from the different major/old religions of the world. Various versions/translations are provided - e.g. there are at least 6 English translations of some of the different versions of the Koran/Qur'an. There is only one version of the Christian bible - the King James Version.
Needs Improvement:(No notes on this as I have not seen any drawbacks in the software or its content, though I would like it to include some other religious works - e.g., Swedenborg's profound religious philosophy.)
Why I think you should use this product:If you are interested in expanding your knowledge of theology, religions, religious books/bibles and comparative theology, then Interfaith Explorer will be of great assistance in this.
Gives you the ability to review and compare a pretty full range of biblical texts in a way that you might not otherwise have been able to do.
How it compares to similar products:(No notes on this as I have not trialled any similar products.)
Conclusions:- As I said in the above quoted post.
Prepare to be somewhat amazed. Well worth at least an exploratory read.
- Incredibly useful, and it's FREE.
- No-fuss, simple and quick download and installation.
Last, but not least, this software and its resources are made accessible to speakers of (so far) 20 different languages: (per
http://bahairesearch.../Pages/Download.aspx)


 Recent Posts
Recent Posts


 That looks awesome! Running out to download and check it out....
That looks awesome! Running out to download and check it out....