101
Living Room / Re: File Encryption - now effectively outlawed in the US?
« on: April 04, 2017, 12:05 PM »
IainB, I'm going to cut your prose short.
You revived the other thread, so that's where I posted objective reasons to avoid the product.
This thread is about a political issue, and thus this thread is where I ask why you're trying to solve a political problem with a (bad) technological solution.
Also...
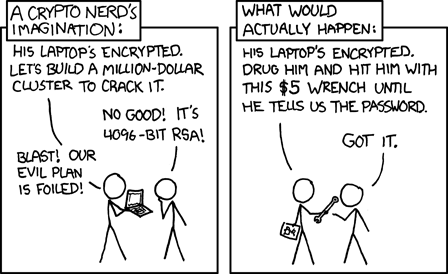
You revived the other thread, so that's where I posted objective reasons to avoid the product.
This thread is about a political issue, and thus this thread is where I ask why you're trying to solve a political problem with a (bad) technological solution.
Also...



